|What is Google hacking?
Google hacking, sometimes, referred to as Google dorking, is an information gathering technique used by an attacker leveraging advanced Google searching techniques. Google hacking search queries can be used to identify security vulnerabilities in web applications, gather information for arbitrary or individual targets, discover error messages disclosing sensitive information, discover files containing credentials and other sensitive data.
The advanced search string crafted by an attacker could be searching for the vulnerable version of a web application, or a specific file-type (.pwd, .sql...) in order to further restrict the search. The search can also be restricted to pages on a specific site, or it can search for specific information across all websites, giving a list of sites that contain the information.
Example
For instance, the following search query will list SQL files (filetype:sql) available that have been indexed by Google on websites where directory listing is enabled (intitle:"index of").
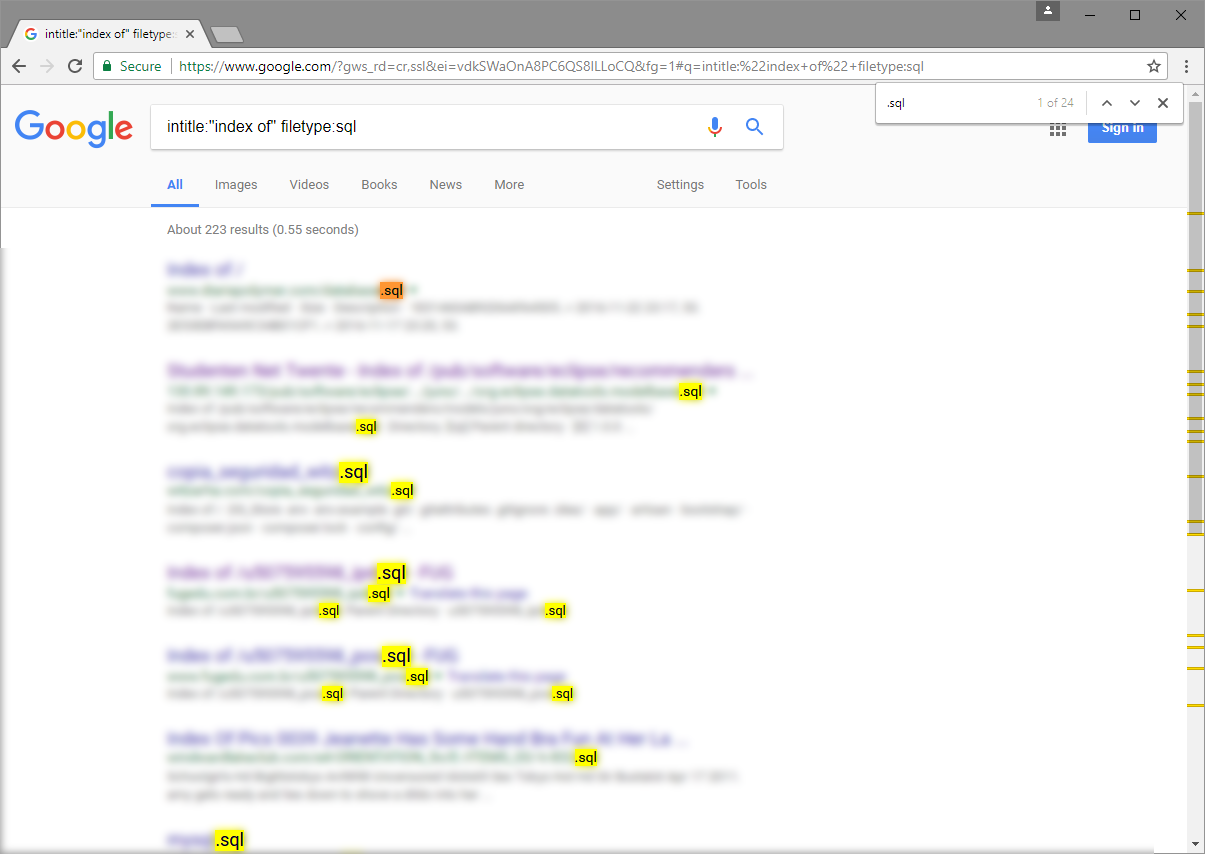
Similarly, the following search query will list publicly accessible phpMyAdmin installations.
Logical operators and symbols
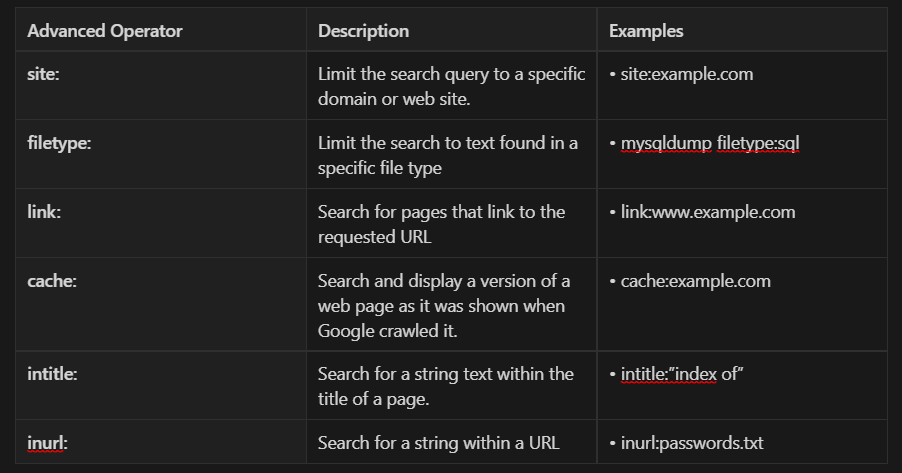
Attackers can take advantage of Google search logical operators such as AND, NOT and OR (case sensitive) as well as operators such as ~, – and *. The following table provides additional information on these operators.
Advanced operators
PREVENTING GOOGLE DORKS
- Encoding/encrypting sensitive data such as usernames, passwords, payment details, messages, addresses, telephone numbers, and so forth.
- Run inquiries against your own site to check whether you can locate any sensitive data. On the off chance that you discover sensitive information, you can remove it from search results by utilizing Google Search Console.
- Protect sensitive content by utilizing a robots.txt document situated in your root-level site catalog. Utilizing robots.txt helps prevent Google from indexing our site, but it can also show an attacker where sensitive data might be located.
- Source: acunetix anthonygaliamov
- Wrote: February 24, 2023 | Esfand 5, 1401
- Updated:
- Posted: February 24, 2023 | Esfand 5, 1401