|UTM
(Unified Threat Management)
Unified threat management (UTM) describes an information security (infosec) system that provides a single point of protection against threats, including viruses and network attacks.
Unlike antivirus tools, a UTM system does not just protect personal computers (PCs) and servers. It protects an entire network and individual users by scanning all network traffic, filtering or blocking potentially dangerous content.
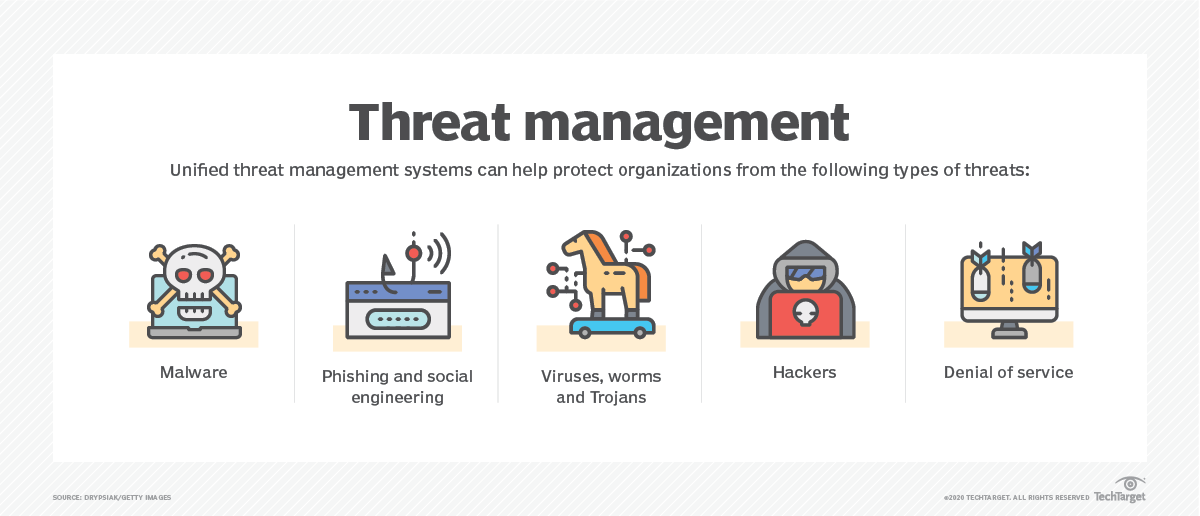
UTM systems combine multiple security features into a single device or software program. This can help because there are five primary kinds of threats that organizations need to protect against:
- malware
- phishing and social engineering
- viruses, worms and Trojans
- hackers
- denial of service (DoS)
How UTM works
A UTM system can identifying weaknesses and threats by using two inspection methods:
- Flow-based inspection: Also known as stream-based inspection, samples data that enters a network security device like firewall. The devices inspect the data for malicious activity, such as viruses.
- Proxy-based inspection: is a network security technique that can be used to examine the contents of packets that pass into and out of a network security device, such as a firewall. By using a proxy server to inspect these packets, the network security device can act as a proxy to reconstruct the content entering the device.
Unified threat management devices
UTM devices are hardware or software that tie together network security features into one simple-to-use, easy-to-manage appliance. In addition to having a firewall, VPN and IPS, every UTM appliance supports network- or cloud-based centralized management.
Is UTM all good
While unified threat management solutions do solve some network security issues, they aren't without some drawbacks, with the biggest one being that the single point of defense that an UTM appliance provides also creates a single point of failure. Because of this, many organizations choose to supplement their UTM device with a second software-based perimeter to stop any malware that got through or around the UTM firewall.
- Source: techtarget | kaspersky
- Wrote: December 10, 2022 | Azar 19, 1401
- Updated:
- Posted: December 10, 2022 | Azar 19, 1401